准备环境
系统: CentOS 6.7 X86_64
OpenVpn: 2.4.4
关闭Selinux
[root@localhost 2.0]# sed -i '/^SELINUX=/c\SELINUX=disabled' /etc/selinux/config
安装epelrpm包,不然没有openvpn这个rpm,安装openvpn相关依赖的包
[root@localhost 2.0]# rpm -ivh http://mirrors.sohu.com/fedora-epel/6/x86_64/epel-release-6-8.noarch.rpm
[root@localhost 2.0]# yum -y install openvpn easy-rsa openssl openssl-devel gcc vim
修改Easy-ras主服务信息.
[root@localhost 2.0]# cd /usr/share/easy-rsa/2.0/
[root@localhost 2.0]# chmod +x *
[root@localhost 2.0]# cp -a vars vars.20180111
[root@localhost 2.0]# vim vars ###找到这个文件修改其中的这几行信息
export KEY_COUNTRY="CN"
export KEY_PROVINCE="SH"
export KEY_CITY="SH"
export KEY_ORG="DFCF"
export KEY_EMAIL="zky.linux@gmail.com"
export KEY_OU="OPS"
[root@localhost 2.0]#
清除keys目录下所有与证书相关的文件,
注意:下面步骤生成的证书和密钥都在/usr/share/easy-rsa/2.0/keys目录里
[root@localhost 2.0]# source vars //提示可以忽略
[root@localhost 2.0]# ./clean-all
[root@localhost 2.0]# ll keys/
生成根证书ca.crt和根密钥ca.key(一路回车即可)
[root@localhost 2.0]# ./build-ca
[root@localhost 2.0]# ll /usr/share/easy-rsa/2.0/keys
总用量 12
-rw-r--r-- 1 root root 1647 1月 12 00:43 ca.crt
-rw------- 1 root root 1704 1月 12 00:43 ca.key
-rw-r--r-- 1 root root 0 1月 12 00:43 index.txt
-rw-r--r-- 1 root root 3 1月 12 00:43 serial
[root@localhost 2.0]#
生成服务端证书
[root@localhost 2.0]# ./build-key-server server
Generating a 2048 bit RSA private key
.+++
....................+++
writing new private key to 'server.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
----- ### 默认全部回车这里
Country Name (2 letter code) [CN]:
State or Province Name (full name) [SH]:
Locality Name (eg, city) [SH]:
Organization Name (eg, company) [DFCF]:
Organizational Unit Name (eg, section) [OPS]:
Common Name (eg, your name or your server's hostname) [server]:
Name [EasyRSA]:
Email Address [zky.linux@gmail.com]:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:password ###需要输入密码
An optional company name []:
Using configuration from /usr/share/easy-rsa/2.0/openssl-1.0.0.cnf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
countryName :PRINTABLE:'CN'
stateOrProvinceName :PRINTABLE:'SH'
localityName :PRINTABLE:'SH'
organizationName :PRINTABLE:'DFCF'
organizationalUnitName:PRINTABLE:'OPS'
commonName :PRINTABLE:'server'
name :PRINTABLE:'EasyRSA'
emailAddress :IA5STRING:'zky.linux@gmail.com'
Certificate is to be certified until Jan 9 16:49:51 2028 GMT (3650 days)
Sign the certificate? [y/n]:y ### 输入Y确认
1 out of 1 certificate requests certified, commit? [y/n]y ### 输入Y确认
Write out database with 1 new entries
Data Base Updated
[root@localhost 2.0]#
为客户端生成证书 (后面要换成账号名+密码认证这一步可以省略。)
创建dh密钥
[root@localhost 2.0]# ./build-dh
Generating DH parameters, 2048 bit long safe prime, generator 2
This is going to take a long time
...............................+...............................................................................................................................................+.+..............................+...................................................................................................................+.................+.............................................................+.+.......................................+.............................................................+...................+..............................................................................................................................................................................................................+.................+.....................................+.....................................+............................................+.....................+..+.............................................................................+....................................................................................................................+..................................................................................................................................................................................................................................................................................+.......................+......+......................................................................................................................+.....................................................+................................................................................................................................................+......................................+..................................................................+........................................+........++*++*
[root@localhost 2.0]#
查看文件是否生成完成
[root@localhost 2.0]# ll keys/
总用量 52
-rw-r--r-- 1 root root 5350 1月 12 00:50 01.pem
-rw-r--r-- 1 root root 1647 1月 12 00:43 ca.crt
-rw------- 1 root root 1704 1月 12 00:43 ca.key
-rw-r--r-- 1 root root 424 1月 12 00:54 dh2048.pem
-rw-r--r-- 1 root root 115 1月 12 00:50 index.txt
-rw-r--r-- 1 root root 21 1月 12 00:50 index.txt.attr
-rw-r--r-- 1 root root 0 1月 12 00:43 index.txt.old
-rw-r--r-- 1 root root 3 1月 12 00:50 serial
-rw-r--r-- 1 root root 3 1月 12 00:43 serial.old
-rw-r--r-- 1 root root 5350 1月 12 00:50 server.crt
-rw-r--r-- 1 root root 1094 1月 12 00:49 server.csr
-rw------- 1 root root 1704 1月 12 00:49 server.key
[root@localhost 2.0]#
将刚才创建完成的key文件复制到openvpn目录下面
[root@localhost 2.0]# cd keys/
[root@localhost keys]# cp -a ca.crt dh2048.pem server.crt server.key /etc/openvpn/
[root@localhost keys]#
修改server.conf配置文件,可以复制简单的模板文件然后修改.如下配置文件是测试成功
[root@localhost keys]# cp -a /usr/share/doc/openvpn-2.4.4/sample/sample-config-files/server.conf /etc/openvpn/
[root@localhost openvpn]# cat server.conf
port 1188
proto udp
dev tun
ca ca.crt
cert server.crt
key server.key # This file should be kept secret
dh dh2048.pem
server 10.8.0.0 255.255.255.0
push "redirect-gateway def1 bypass-dhcp"
push "dhcp-option DNS 202.96.209.133"
push "dhcp-option DNS 8.8.8.8"
client-to-client
keepalive 10 120
comp-lzo
persist-key
persist-tun
status openvpn-status.log
verb 5
log /var/log/openvpn.log
log-append /var/log/openvpn.log
client-cert-not-required
auth-user-pass-verify /etc/openvpn/checkpsw.sh via-env
script-security 3
username-as-common-name
[root@localhost openvpn]#
修改用户名密码配置文件,并且授权
下载脚本
[root@localhost openvpn]# wget http://code.taobao.org/svn/OpenwrtVpn/checkpsw.sh
修改配置文件中PASSFILE这一行文件,并授权.如下:
[root@localhost openvpn]# vim /etc/openvpn/checkpsw.sh
PASSFILE="/etc/openvpn/userfile.sh" ### 修改其中的一行文件
[root@localhost openvpn]#
[root@localhost openvpn]# chmod +x /etc/openvpn/checkpsw.sh
[root@localhost openvpn]#
创建用户文件,格式是"用户名” “空格” “密码”
[root@localhost openvpn]# cat userfile.sh
test test123
[root@localhost openvpn]# chown nobody:nobody userfile.sh
[root@localhost openvpn]#
配置服务器转发
[root@localhost openvpn]# echo "1" > /proc/sys/net/ipv4/ip_forward
重启openvpn服务
/etc/init.d/openvpn start
chkconfig openvpn on
设置防火墙转发,在原来的基础上增加
iptables -F , iptables -X iptables -Z
[root@localhost openvpn]# cat /etc/sysconfig/iptables
# Generated by iptables-save v1.4.7 on Thu Mar 22 15:52:09 2018
*nat
:PREROUTING ACCEPT [11:899]
:POSTROUTING ACCEPT [0:0]
:OUTPUT ACCEPT [2:142]
-A POSTROUTING -s 10.8.0.0/24 -j MASQUERADE
-A POSTROUTING -o em1 -j SNAT --to-source SERVER-IP(上网的IP地址)
COMMIT
# Completed on Thu Mar 22 15:52:09 2018
# Generated by iptables-save v1.4.7 on Thu Mar 22 15:52:09 2018
*filter
:INPUT ACCEPT [94:7799]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [48:5876]
-A FORWARD -i em1 -o tun0 -m state --state RELATED,ESTABLISHED -j ACCEPT
-A FORWARD -i tun0 -o em1 -j ACCEPT
-A FORWARD -s 10.8.0.0/24 -j ACCEPT
-A FORWARD -m state --state RELATED,ESTABLISHED -j ACCEPT
COMMIT
# Completed on Thu Mar 22 15:52:09 2018
[root@localhost openvpn]#
[root@localhost openvpn]# /etc/rc.d/init.d/iptables save
iptables:将防火墙规则保存到 /etc/sysconfig/iptables: [确定]
[root@localhost openvpn]# /etc/rc.d/init.d/iptables restart
iptables:将链设置为政策 ACCEPT:filter [确定]
iptables:清除防火墙规则: [确定]
iptables:正在卸载模块: [确定]
iptables:应用防火墙规则: [确定]
[root@localhost openvpn]#
客户端文件配置
1. copy服务器上的ca.crt配置文件,给客户端
[root@localhost openvpn]# pwd
/etc/openvpn
[root@localhost openvpn]# ll ca.crt
-rw-r--r-- 1 root root 1647 1月 12 00:43 ca.crt
[root@localhost openvpn]#
2. 安装OpenVpn客户端之后,需要把sample-config中的client.ovpn模板复制到config中目录下面并且修改
3. 修改客户端openvpn客户端中的config配置文件如下:
[root@localhost openvpn]# cat ~/Desktop/windows客户端安装包/config/client.ovpn
client
dev tun
proto udp
remote openvpnserver 1188
resolv-retry infinite
nobind
persist-key
persist-tun
ca ca.crt
comp-lzo
verb 5
route-delay 2
auth-user-pass
auth-nocache
reneg-sec 360000
user nobody
group nobody
[root@localhost openvpn]#
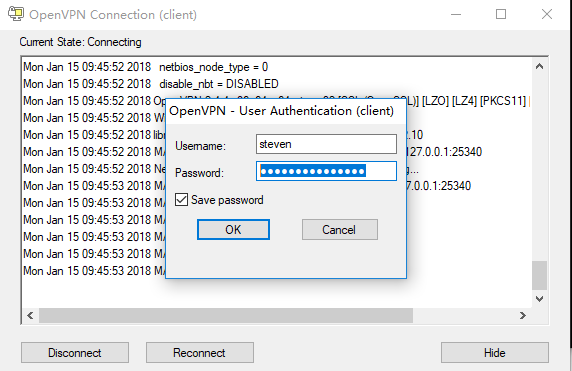
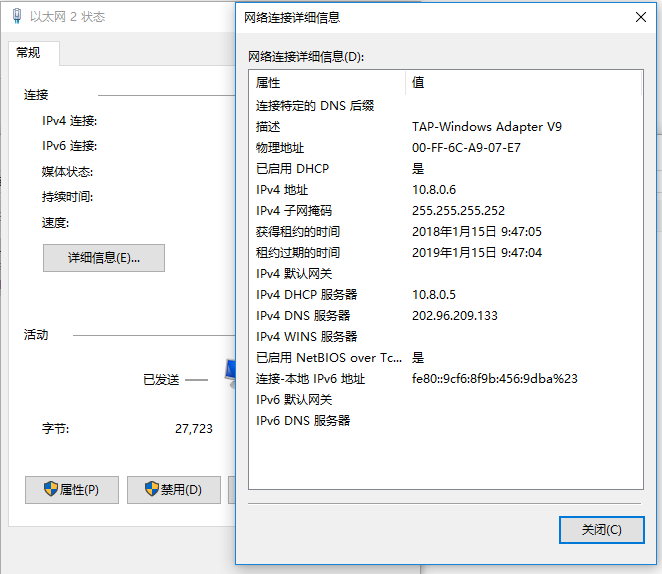
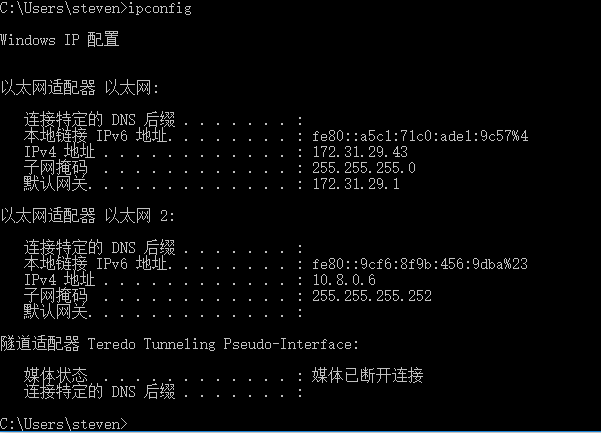
登陆状态如下图所示: